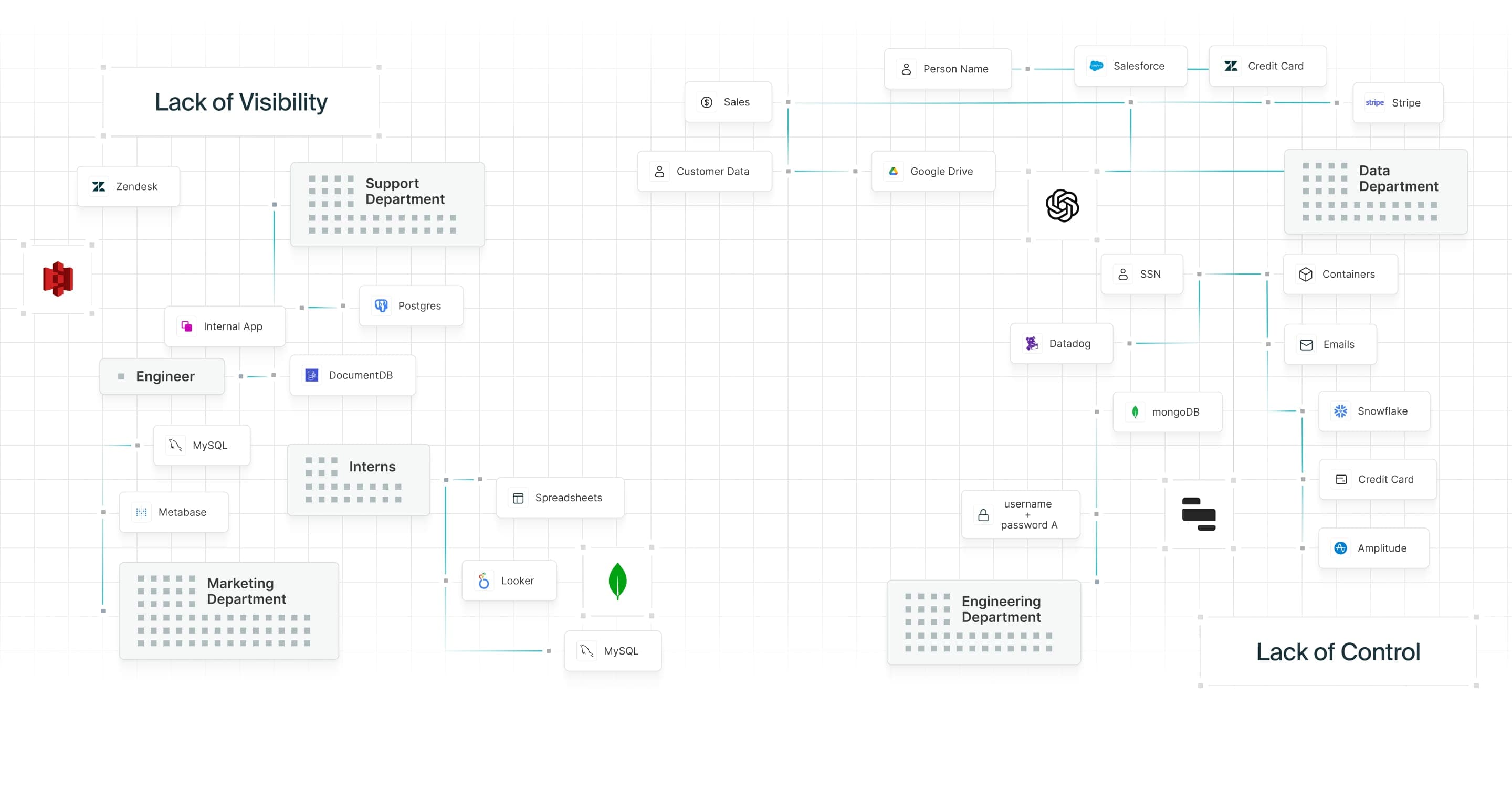
The past decade has seen incredible innovation in the data stack, but also increased complexity. Without a clear picture and control of their data, enterprises face greater risk than ever before.
The Growing Data Problem
The modern data stack in the cloud certainly does better enable data-driven decision making. But it also multiplies the vulnerabilities to data breaches – it makes it complex to know where data lives and who can access it.
Formal empowers security teams to understand their data flows in real-time and enforce access policies that actually work.
Formal Data Graph
The Formal Data Graph dynamically learns from your organization’s data flow, classifies data, and automatically recommends and enforces least-privilege policies in real time.
The Formal Data Graph helps you understand the who, what, and where of data consumption across your organization.
Agree on a strategy that secures your data and brings your teams closer together.
Comment on logs and policies and collaborate directly via Slack. Task colleagues in Jira and Linear directly from the platform. Code and No-code options allow everyone to collaborate.

Control your entire data stack in one place
The Formal AI Engine recommends you the policies to enforce based on historical trend to enforce least-privilege access and decrease potential blast radius.

Game changers run on Formal.
Data Security as Code
Formal helps security teams to win the heart and minds of DevOps thanks to an API-first design that seamlessly integrates with your stack. Choose your IaC, pick your VPC, and deploy a single distroless Docker image containing only a single statically linked binary for unrivaled simplicity and security.
terraform {
required_providers {
formal = {
source = "formalco/formal"
version = "~>4.0.0"
}
}
required_version = ">= 0.14.9"
}
provider "formal" {
api_key = var.formal_api_key
}
resource "formal_sidecar" "main" {
name = var.name
technology = "mysql"
hostname = var.mysql_sidecar_hostname
}
resource "formal_resource" "main" {
technology = "mysql"
name = var.name
hostname = var.mysql_hostname
port = var.main_port
}
resource "formal_sidecar_resource_link" "main" {
resource_id = formal_resource.main.id
sidecar_id = formal_sidecar.main.id
port = 3306
}
# Native Role
resource "formal_native_user" "main_mysql" {
resource_id = formal_datastore.main.id
native_user_id = var.mysql_username
native_user_secret = var.mysql_password
use_as_default = true
// per sidecar, exactly one native role must be marked
as the default.
}
func main() {
pulumi.Run(func(ctx *pulumi.Context) error {
cfg := config.New(ctx, "")
// Load required configuration
formalApiKey := cfg.Require("formal_api_key")
name := cfg.Require("name")
mysqlSidecarHostname := cfg.Require("mysql_sidecar_hostname")
// Initialize the Formal provider
provider, err := formal.NewProvider(ctx, "formal", &formal.ProviderArgs{
ApiKey: pulumi.String(formalApiKey),
})
if err != nil {
return err
}
// Create the formal_sidecar resource
sidecar, err := formal.NewSidecar(ctx, "main", &formal.SidecarArgs{
Name: pulumi.String(name),
Technology: pulumi.String("mysql"),
Hostname: pulumi.String(mysqlSidecarHostname),
}, pulumi.Provider(provider))
if err != nil {
return err
}
// Create the formal_resource resource
resource, err := formal.NewResource(ctx, "main", &formal.ResourceArgs{
Technology: pulumi.String("mysql"),
Name: pulumi.String(name),
Hostname: pulumi.String(mysqlHostname),
Port: pulumi.Int(mainPort),
}, pulumi.Provider(provider))
if err != nil {
return err
}
// Create the formal_sidecar_resource_link resource
_, err = formal.NewSidecarResourceLink(ctx, "main", &formal.SidecarResourceLinkArgs{
ResourceId: resource.ID(),
SidecarId: sidecar.ID(),
Port: pulumi.Int(3306),
}, pulumi.Provider(provider))
if err != nil {
return err
}
// Create the formal_native_user resource
_, err = formal.NewNativeUser(ctx, "main_mysql", &formal.NativeUserArgs{
ResourceId: resource.ID(),
NativeUserId: pulumi.String(mysqlUsername),
NativeUserSecret: pulumi.String(mysqlPassword),
UseAsDefault: pulumi.Bool(true),
}, pulumi.Provider(provider))
if err != nil {
return err
}
return nil
})
}
import * as formal_sdk from 'formal-sdk';
import { CreateSidecarRequest } from 'formal-sdk/gen/admin/v1/sidecar_pb';
// Get the API key from environment variables
const apiKey = process.env.API_KEY;
if (!apiKey) {
throw new Error('API_KEY environment variable is not set');
}
// Initialize the Formal client
const formalClient = new formal_sdk.Client(apiKey);
// Create a sidecar
const request = new CreateSidecarRequest({
name: '<string>',
resource_id: '<string>',
hostname: '<string>',
technology: '<string>',
termination_protection: <boolean>
});
formalClient.SidecarClient.CreateSidecar(request)
.then(response => {
console.log('Sidecar created successfully:', response);
})
.catch(error => {
console.error('Error creating sidecar:', error);
});
import os
import formal_sdk
from formal_sdk.gen.admin.v1.sidecar_pb2 import CreateSidecarRequest
api_key = os.environ.get('API_KEY')
formal_client = formal_sdk.Client(api_key) # Formal base client
formal_client.SidecarClient.CreateSidecar(
CreateSidecarRequest("name": <string>,
"resource_id": <string>,
"hostname": <string>,
"technology": <string>,
"termination_protection": <bool>)
)
We secure the flow of data — without being in the flow.
Formal is designed with enterprise-grade security. Our Proxy is deployed in your VPC, ensuring only you control your data. Reliability is our top concern and our Proxy is designed to be highly available.



